|
VeteranX
|
lately people have been complaining about the stability of the servers. I've noticed that branzone doesn't offer ddos protection on their Tribes 1 servers unless its the one they host in New York.
I have 3 main theories on the culprits and what/who it could be. Since I'm not an experienced IT professional or anything, these are merely hunches or theories. Yes also nothing short of a s_hit post.
- Devs from other tribes like franchises ddosing the servers (to get ppl to quit and play their game maybe or buy midair?)
- poisonous fish. an IT professional for the Tennessee Department of Homeland Security.
- Some other disgruntled user on TW (you know who).
Illinois currently in fourth place in the US at 491,782 cyber attacks in 24 hours.
source: Page Forbidden | Error 403 | Akamai
also I assume that the master server could be under attack as well. idk 
maybe I'm just paranoid and I need to wear my tinfoil hat.  |
|
|
|
AlwaysCryingXX
Contributor
|
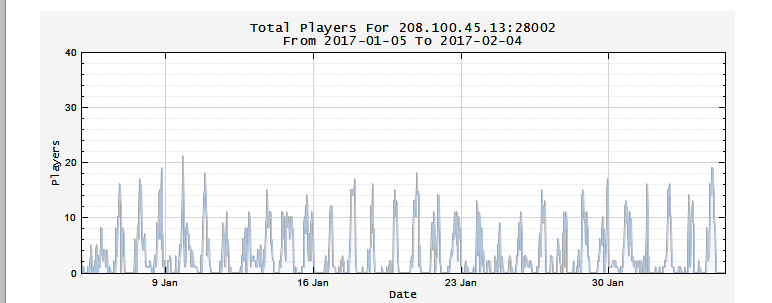
server seems fine tbh
 |
|
|
|
VeteranXV
|
I've been getting lag spikes recently and trigger lag. Not sure if its on my end or server's.  |
|
|
|
AlwaysCryingXX
Contributor
|
i restart the server/ bugs_ should still have access if it keeps up ask him or even opsayo meph stork etc
lestat has access too
anyway there shouldnt be any lag so if its on ur end maybe try a tracert
http://www.youtube.com/watch?v=VwTNOxJXMYM |
|
|
|
VeteranX
|
yeah i can't seem to complete a normal tracert. It times out everytime. Comcast also masking the first hop when it does work. I guess it would help to say I'm using hotspot service. However it used to work flawlessly in the past when I first started using it.
I changed my computers network settings to communicate with verizons protected dns servers which helped make my online browsing better.
I suppose its probably all on my end. Maybe I'm being targeted since I don't have a hardware firewall and essentially using the hotspot feature from someone elses router.
edit: yeah i feel like an idiot. Admin plz edit post title to "shift is too poor to pay for real isp"
|
|
|
|
VeteranXV
|
tribes dead
rip tribe
But the other night, all branzone servers were pinging 200+ for me. Everyone else was fine. It was branzone servers in tribes AND tribes2 that were pinging 200-380. No one else had pings over 60. I could join RPG servers with normal ping.
|
|
|
|
VeteranXX
|
Quote:
Originally Posted by S_hift

I changed my computers network settings to communicate with verizons protected dns servers which helped make my online browsing better.
I suppose its probably all on my end. Maybe I'm being targeted since I don't have a hardware firewall and essentially using the hotspot feature from someone elses router.
edit: yeah i feel like an idiot. Admin plz edit post title to "shift is too poor to pay for real isp"
|
lots of routers either ignore ICMP (pings, traceroutes) or set them at a low priority, the only ping you should really care about in a traceroute is the last one to the destination - if that one is good, none of the others matter.
if the final destination ping is ****ty, then you look at previous hops and try to find the one where they all increase from
but if a hop (say your comcast default gateway) doesn't reply, that's pretty normal (ICMP ignored). its also pretty normal to see higher pings mid-way thru the trace than it is at the final - that's usually low priority ICMP, not an actual bad ping
Quote:
Originally Posted by Odio

But the other night, all branzone servers were pinging 200+ for me. Everyone else was fine. It was branzone servers in tribes AND tribes2 that were pinging 200-380. No one else had pings over 60. I could join RPG servers with normal ping.
|
sounds like a congested route from you to some part of branzone that your ISP detected and re-routed. unless it keeps happening i wouldn't worry about a day or two of poor routing
|
|
|
|
VeteranX
|
heres a little more info. Not sure what you can gather from it groove but it would help.
Code:
Starting Nmap 7.40 ( https://nmap.org ) at 2017-02-04 18:30 Eastern Standard Time
NSE: Loaded 271 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 18:30
NSE: [mrinfo] Nsock connect failed immediately
NSE: [mtrace] A source IP must be provided through fromip argument.
NSE: [shodan-api] Error: Please specify your ShodanAPI key with the shodan-api.apikey argument
Completed NSE at 18:30, 10.49s elapsed
Initiating NSE at 18:30
Completed NSE at 18:30, 0.00s elapsed
Initiating NSE at 18:30
Completed NSE at 18:30, 0.00s elapsed
Pre-scan script results:
| knx-gateway-discover:
|_ ERROR: Couldn't get interface for 224.0.23.12
| targets-asn:
|_ targets-asn.asn is a mandatory parameter
Initiating Ping Scan at 18:30
Scanning 208.100.60.6 [7 ports]
Completed Ping Scan at 18:30, 0.09s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 18:30
Completed Parallel DNS resolution of 1 host. at 18:30, 0.06s elapsed
Initiating SYN Stealth Scan at 18:30
Scanning www.branzone.com (208.100.60.6) [1000 ports]
Discovered open port 443/tcp on 208.100.60.6
Discovered open port 995/tcp on 208.100.60.6
Discovered open port 587/tcp on 208.100.60.6
Discovered open port 80/tcp on 208.100.60.6
Discovered open port 143/tcp on 208.100.60.6
Discovered open port 110/tcp on 208.100.60.6
Discovered open port 993/tcp on 208.100.60.6
Discovered open port 26/tcp on 208.100.60.6
Discovered open port 465/tcp on 208.100.60.6
Completed SYN Stealth Scan at 18:30, 20.26s elapsed (1000 total ports)
Initiating UDP Scan at 18:30
Scanning www.branzone.com (208.100.60.6) [1000 ports]
Completed UDP Scan at 18:30, 7.27s elapsed (1000 total ports)
Initiating Service scan at 18:30
Scanning 1009 services on www.branzone.com (208.100.60.6)
Service scan Timing: About 0.99% done
Service scan Timing: About 3.96% done; ETC: 19:52 (1:18:44 remaining)
Service scan Timing: About 6.94% done; ETC: 19:41 (1:05:17 remaining)
Service scan Timing: About 9.91% done; ETC: 19:36 (0:59:05 remaining)
Service scan Timing: About 12.88% done; ETC: 19:34 (0:55:00 remaining)
Service scan Timing: About 15.86% done; ETC: 19:32 (0:51:44 remaining)
Service scan Timing: About 20.71% done; ETC: 19:26 (0:43:53 remaining)
Service scan Timing: About 24.58% done; ETC: 19:24 (0:40:21 remaining)
Service scan Timing: About 24.78% done; ETC: 19:30 (0:44:26 remaining)
Service scan Timing: About 29.53% done; ETC: 19:26 (0:38:58 remaining)
Service scan Timing: About 33.50% done; ETC: 19:24 (0:35:48 remaining)
Service scan Timing: About 39.44% done; ETC: 19:24 (0:32:40 remaining)
Service scan Timing: About 45.39% done; ETC: 19:25 (0:29:31 remaining)
Service scan Timing: About 51.34% done; ETC: 19:25 (0:26:20 remaining)
Service scan Timing: About 57.28% done; ETC: 19:25 (0:23:09 remaining)
Service scan Timing: About 63.23% done; ETC: 19:25 (0:19:57 remaining)
Service scan Timing: About 69.08% done; ETC: 19:25 (0:16:49 remaining)
Service scan Timing: About 75.02% done; ETC: 19:25 (0:13:35 remaining)
Service scan Timing: About 80.97% done; ETC: 19:25 (0:10:21 remaining)
Service scan Timing: About 86.92% done; ETC: 19:25 (0:07:07 remaining)
Service scan Timing: About 92.86% done; ETC: 19:25 (0:03:53 remaining)
Service scan Timing: About 98.81% done; ETC: 19:25 (0:00:39 remaining)
Completed Service scan at 19:26, 3317.69s elapsed (1009 services on 1 host)
Initiating OS detection (try #1) against www.branzone.com (208.100.60.6)
Initiating Traceroute at 19:26
Completed Traceroute at 19:26, 3.17s elapsed
NSE: Script scanning 208.100.60.6.
Initiating NSE at 19:26
NSE: [ip-geolocation-maxmind] You must specify a Maxmind database file with the maxmind_db argument.
NSE: [ip-geolocation-maxmind] Download the database from http://dev.maxmind.com/geoip/legacy/geolite/
Completed NSE at 19:28, 102.40s elapsed
Initiating NSE at 19:28
Completed NSE at 19:28, 52.21s elapsed
Initiating NSE at 19:28
Completed NSE at 19:29, 3.28s elapsed
Nmap scan report for www.branzone.com (208.100.60.6)
NSOCK ERROR [3369.2990s] mksock_bind_addr(): Bind to 0.0.0.0:500 failed (IOD #35): An attempt was made to access a socket in a way forbidden by its access permissions. (10013)
NSOCK ERROR [3370.9470s] mksock_bind_addr(): Bind to 0.0.0.0:500 failed (IOD #39): An attempt was made to access a socket in a way forbidden by its access permissions. (10013)
NSOCK ERROR [3371.4940s] mksock_bind_addr(): Bind to 0.0.0.0:500 failed (IOD #40): An attempt was made to access a socket in a way forbidden by its access permissions. (10013)
NSOCK ERROR [3372.4750s] mksock_bind_addr(): Bind to 0.0.0.0:500 failed (IOD #41): An attempt was made to access a socket in a way forbidden by its access permissions. (10013)
NSOCK ERROR [3374.7240s] mksock_bind_addr(): Bind to 0.0.0.0:500 failed (IOD #65): An attempt was made to access a socket in a way forbidden by its access permissions. (10013)
NSOCK ERROR [3411.0210s] mksock_bind_addr(): Bind to 0.0.0.0:500 failed (IOD #259): An attempt was made to access a socket in a way forbidden by its access permissions. (10013)
NSOCK ERROR [3411.3630s] mksock_bind_addr(): Bind to 0.0.0.0:500 failed (IOD #262): An attempt was made to access a socket in a way forbidden by its access permissions. (10013)
Host is up (0.13s latency).
Not shown: 1000 open|filtered ports, 989 filtered ports
PORT STATE SERVICE VERSION
20/tcp closed ftp-data
26/tcp open smtp Exim smtpd 4.88
| banner: 220-web.branzone.com ESMTP Exim 4.88 #1 Sat, 04 Feb 2017 18:27:
|_01 -0600 \x0D\x0A220-We do not authorize the use of this system to t...
| smtp-commands: web.branzone.com Hello c-68-33-93-201.hsd1.va.comcast.net [68.33.93.201], SIZE 52428800, 8BITMIME, PIPELINING, AUTH PLAIN LOGIN, CHUNKING, STARTTLS, HELP,
|_ Commands supported: AUTH STARTTLS HELO EHLO MAIL RCPT DATA BDAT NOOP QUIT RSET HELP
| ssl-cert: Subject: commonName=mail.branzone.com
| Subject Alternative Name: DNS:mail.branzone.com
| Issuer: commonName=RapidSSL SHA256 CA - G3/organizationName=GeoTrust Inc./countryName=US
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2015-04-05T03:37:51
| Not valid after: 2018-04-07T12:28:10
| MD5: 810c 5a6a 2b9d f858 932a f351 4e5d 5bef
|_SHA-1: 98d6 8f15 7de2 4da0 c8ab 6f65 f97f 138f 45c7 ff16
|_ssl-date: 2017-02-05T00:27:07+00:00; -2s from scanner time.
53/tcp closed domain
80/tcp open http Apache httpd
|_http-comments-displayer: Couldn't find any comments.
|_http-date: Sun, 05 Feb 2017 00:26:38 GMT; -2s from local time.
| http-headers:
| Date: Sun, 05 Feb 2017 00:26:38 GMT
| Server: Apache
| Location: https://www.branzone.com/
| Content-Length: 233
| Connection: close
| Content-Type: text/html; charset=iso-8859-1
|
|_ (Request type: GET)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-mobileversion-checker: No mobile version detected.
|_http-referer-checker: Couldn't find any cross-domain scripts.
|_http-server-header: Apache
|_http-title: Did not follow redirect to https://www.branzone.com/
| http-traceroute:
|_ Possible reverse proxy detected.
| http-useragent-tester:
|
| Allowed User Agents:
| Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)
| libwww
| lwp-trivial
| libcurl-agent/1.0
| PHP/
| Python-urllib/2.5
| GT::WWW
| Snoopy
| MFC_Tear_Sample
| HTTP::Lite
| PHPCrawl
| URI::Fetch
| Zend_Http_Client
| http client
| PECL::HTTP
| Wget/1.13.4 (linux-gnu)
| WWW-Mechanize/1.34
|_
|_http-xssed: No previously reported XSS vuln.
110/tcp open pop3 Dovecot pop3d
|_banner: +OK Dovecot ready.
|_pop3-capabilities: UIDL CAPA TOP PIPELINING USER RESP-CODES AUTH-RESP-CODE SASL(PLAIN LOGIN) STLS
| ssl-cert: Subject: commonName=mail.branzone.com
| Subject Alternative Name: DNS:mail.branzone.com
| Issuer: commonName=RapidSSL SHA256 CA - G3/organizationName=GeoTrust Inc./countryName=US
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2015-04-05T03:37:51
| Not valid after: 2018-04-07T12:28:10
| MD5: 810c 5a6a 2b9d f858 932a f351 4e5d 5bef
|_SHA-1: 98d6 8f15 7de2 4da0 c8ab 6f65 f97f 138f 45c7 ff16
|_ssl-date: 2017-02-05T00:27:14+00:00; -2s from scanner time.
143/tcp open imap Dovecot imapd
| banner: * OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID
|_ENABLE IDLE NAMESPACE STARTTLS AUTH=PLAIN AUTH=LOGIN] Dovecot ready.
|_imap-capabilities: OK post-login NAMESPACE listed AUTH=LOGINA0001 STARTTLS SASL-IR IMAP4rev1 LOGIN-REFERRALS Pre-login LITERAL+ ENABLE IDLE more capabilities AUTH=PLAIN ID have
| ssl-cert: Subject: commonName=mail.branzone.com
| Subject Alternative Name: DNS:mail.branzone.com
| Issuer: commonName=RapidSSL SHA256 CA - G3/organizationName=GeoTrust Inc./countryName=US
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2015-04-05T03:37:51
| Not valid after: 2018-04-07T12:28:10
| MD5: 810c 5a6a 2b9d f858 932a f351 4e5d 5bef
|_SHA-1: 98d6 8f15 7de2 4da0 c8ab 6f65 f97f 138f 45c7 ff16
|_ssl-date: 2017-02-05T00:26:42+00:00; -2s from scanner time.
443/tcp open ssl/http Apache httpd (PHP 5.6.29)
| http-backup-finder:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=www.branzone.com
| https://www.branzone.com/announcements/10/ARK-Survival-Evolved-Game-Servers-Now-Available.bak
| https://www.branzone.com/announcements/10/ARK-Survival-Evolved-Game-Servers-Now-Available.html~
| https://www.branzone.com/announcements/10/ARK-Survival-Evolved-Game-Servers-Now-Available copy.html
| https://www.branzone.com/announcements/10/Copy of ARK-Survival-Evolved-Game-Servers-Now-Available.html
| https://www.branzone.com/announcements/10/Copy (2) of ARK-Survival-Evolved-Game-Servers-Now-Available.html
| https://www.branzone.com/announcements/10/ARK-Survival-Evolved-Game-Servers-Now-Available.html.1
| https://www.branzone.com/announcements/10/ARK-Survival-Evolved-Game-Servers-Now-Available.html.~1~
| https://www.branzone.com/domainchecker.bak
| https://www.branzone.com/domainchecker.php~
| https://www.branzone.com/domainchecker copy.php
| https://www.branzone.com/Copy of domainchecker.php
| https://www.branzone.com/Copy (2) of domainchecker.php
| https://www.branzone.com/domainchecker.php.1
| https://www.branzone.com/domainchecker.php.~1~
| https://www.branzone.com/templates/branzone/css/bootstrap.bak
| https://www.branzone.com/templates/branzone/css/bootstrap.css~
| https://www.branzone.com/templates/branzone/css/bootstrap copy.css
| https://www.branzone.com/templates/branzone/css/Copy of bootstrap.css
| https://www.branzone.com/templates/branzone/css/Copy (2) of bootstrap.css
| https://www.branzone.com/templates/branzone/css/bootstrap.css.1
| https://www.branzone.com/templates/branzone/css/bootstrap.css.~1~
| https://www.branzone.com/includes/verifyimage.bak
| https://www.branzone.com/includes/verifyimage.php~
| https://www.branzone.com/includes/verifyimage copy.php
| https://www.branzone.com/includes/Copy of verifyimage.php
| https://www.branzone.com/includes/Copy (2) of verifyimage.php
| https://www.branzone.com/includes/verifyimage.php.1
|_ https://www.branzone.com/includes/verifyimage.php.~1~
| http-cakephp-version: Version of codebase: 1.1.x, 1.2.x
|_Version of icons: 1.3.x
|_http-comments-displayer: Couldn't find any comments.
|_http-date: Sun, 05 Feb 2017 00:26:45 GMT; -13s from local time.
|_http-favicon: Unknown favicon MD5: CC05FBE818D9FAFC8A382087CA698AEC
| http-headers:
| Date: Sun, 05 Feb 2017 00:27:05 GMT
| Server: Apache
| X-Powered-By: PHP/5.6.29
| Set-Cookie: WHMCSdkUt8vhdACYy=15af404f1c567b8369838bec2f4e5532; path=/; secure; HttpOnly
| Expires: Thu, 19 Nov 1981 08:52:00 GMT
| Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
| Pragma: no-cache
| Strict-Transport-Security: \xE2\x80\x9Cmax-age=31536000\xE2\x80\xB3
| Connection: close
| Content-Type: text/html; charset=utf-8
|
|_ (Request type: HEAD)
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-mobileversion-checker: No mobile version detected.
|_http-php-version: Version from header x-powered-by: PHP/5.6.29
|_http-referer-checker: Couldn't find any cross-domain scripts.
|_http-server-header: Apache
|_http-title: Branzone.com - Web Hosting, Game Servers, Voice Servers
| http-traceroute:
|_ Possible reverse proxy detected.
| http-useragent-tester:
|
| Allowed User Agents:
| Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)
| libwww
| lwp-trivial
| libcurl-agent/1.0
| PHP/
| Python-urllib/2.5
| GT::WWW
| Snoopy
| MFC_Tear_Sample
| HTTP::Lite
| PHPCrawl
| URI::Fetch
| Zend_Http_Client
| http client
| PECL::HTTP
| Wget/1.13.4 (linux-gnu)
| WWW-Mechanize/1.34
|_
|_http-xssed: No previously reported XSS vuln.
| ssl-cert: Subject: commonName=www.branzone.com/organizationName=Branzone, Inc./stateOrProvinceName=Texas/countryName=US
| Subject Alternative Name: DNS:www.branzone.com, DNS:branzone.com
| Issuer: commonName=GeoTrust EV SSL CA - G4/organizationName=GeoTrust Inc./countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2015-08-14T00:00:00
| Not valid after: 2017-09-12T23:59:59
| MD5: 9956 2083 0e17 af83 29cc e74b ba31 536d
|_SHA-1: c20d 7c9c 28e4 b4e1 d8c1 600f 3adb 9f9b f3cc 9e56
|_ssl-date: 2017-02-05T00:27:05+00:00; -2s from scanner time.
465/tcp open ssl/smtp Exim smtpd 4.88
| banner: 220-web.branzone.com ESMTP Exim 4.88 #1 Sat, 04 Feb 2017 18:26:
|_31 -0600 \x0D\x0A220-We do not authorize the use of this system to t...
| smtp-commands: web.branzone.com Hello c-68-33-93-201.hsd1.va.comcast.net [68.33.93.201], SIZE 52428800, 8BITMIME, PIPELINING, AUTH PLAIN LOGIN, CHUNKING, HELP,
|_ Commands supported: AUTH HELO EHLO MAIL RCPT DATA BDAT NOOP QUIT RSET HELP
| ssl-cert: Subject: commonName=mail.branzone.com
| Subject Alternative Name: DNS:mail.branzone.com
| Issuer: commonName=RapidSSL SHA256 CA - G3/organizationName=GeoTrust Inc./countryName=US
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2015-04-05T03:37:51
| Not valid after: 2018-04-07T12:28:10
| MD5: 810c 5a6a 2b9d f858 932a f351 4e5d 5bef
|_SHA-1: 98d6 8f15 7de2 4da0 c8ab 6f65 f97f 138f 45c7 ff16
|_ssl-date: 2017-02-05T00:26:30+00:00; -2s from scanner time.
587/tcp open smtp Exim smtpd 4.88
| banner: 220-web.branzone.com ESMTP Exim 4.88 #1 Sat, 04 Feb 2017 18:26:
|_49 -0600 \x0D\x0A220-We do not authorize the use of this system to t...
| smtp-commands: web.branzone.com Hello c-68-33-93-201.hsd1.va.comcast.net [68.33.93.201], SIZE 52428800, 8BITMIME, PIPELINING, AUTH PLAIN LOGIN, CHUNKING, STARTTLS, HELP,
|_ Commands supported: AUTH STARTTLS HELO EHLO MAIL RCPT DATA BDAT NOOP QUIT RSET HELP
| ssl-cert: Subject: commonName=mail.branzone.com
| Subject Alternative Name: DNS:mail.branzone.com
| Issuer: commonName=RapidSSL SHA256 CA - G3/organizationName=GeoTrust Inc./countryName=US
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2015-04-05T03:37:51
| Not valid after: 2018-04-07T12:28:10
| MD5: 810c 5a6a 2b9d f858 932a f351 4e5d 5bef
|_SHA-1: 98d6 8f15 7de2 4da0 c8ab 6f65 f97f 138f 45c7 ff16
|_ssl-date: 2017-02-05T00:26:51+00:00; -2s from scanner time.
993/tcp open ssl/imap Dovecot imapd
| banner: * OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID
|_ENABLE IDLE NAMESPACE AUTH=PLAIN AUTH=LOGIN] Dovecot ready.
|_imap-capabilities: OK post-login NAMESPACE listed AUTH=LOGINA0001 SASL-IR IMAP4rev1 LOGIN-REFERRALS Pre-login LITERAL+ ENABLE IDLE more capabilities AUTH=PLAIN ID have
| ssl-cert: Subject: commonName=mail.branzone.com
| Subject Alternative Name: DNS:mail.branzone.com
| Issuer: commonName=RapidSSL SHA256 CA - G3/organizationName=GeoTrust Inc./countryName=US
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2015-04-05T03:37:51
| Not valid after: 2018-04-07T12:28:10
| MD5: 810c 5a6a 2b9d f858 932a f351 4e5d 5bef
|_SHA-1: 98d6 8f15 7de2 4da0 c8ab 6f65 f97f 138f 45c7 ff16
|_ssl-date: 2017-02-05T00:27:10+00:00; -2s from scanner time.
995/tcp open ssl/pop3 Dovecot pop3d
|_banner: +OK Dovecot ready.
|_pop3-capabilities: UIDL SASL(PLAIN LOGIN) CAPA USER RESP-CODES AUTH-RESP-CODE TOP PIPELINING
| ssl-cert: Subject: commonName=mail.branzone.com
| Subject Alternative Name: DNS:mail.branzone.com
| Issuer: commonName=RapidSSL SHA256 CA - G3/organizationName=GeoTrust Inc./countryName=US
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2015-04-05T03:37:51
| Not valid after: 2018-04-07T12:28:10
| MD5: 810c 5a6a 2b9d f858 932a f351 4e5d 5bef
|_SHA-1: 98d6 8f15 7de2 4da0 c8ab 6f65 f97f 138f 45c7 ff16
|_ssl-date: 2017-02-05T00:26:37+00:00; -2s from scanner time.
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3.4
OS details: Linux 3.4
Uptime guess: 0.065 days (since Sat Feb 04 17:55:27 2017)
Network Distance: 7 hops
TCP Sequence Prediction: Difficulty=258 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Host: web.branzone.com
Host script results:
| asn-query:
| BGP: 208.100.0.0/18 | Country: US
| Origin AS: 32748 - STEADFAST - Steadfast, US
|_ Peer AS: 1299 2381 2603 2914 3356 6453
|_clock-skew: mean: -3s, deviation: 3s, median: -2s
| fcrdns:
| www.branzone.com:
| status: pass
| addresses:
|_ 208.100.60.6
|_firewalk: ERROR: Script execution failed (use -d to debug)
|_hostmap-robtex: ERROR: Script execution failed (use -d to debug)
| ip-geolocation-geoplugin:
|_208.100.60.6
|_ipidseq: ERROR: Script execution failed (use -d to debug)
|_path-mtu: ERROR: Script execution failed (use -d to debug)
|_qscan: ERROR: Script execution failed (use -d to debug)
| traceroute-geolocation:
| HOP RTT ADDRESS GEOLOCATION
| 1 ...
| 2 ...
| 3 ...
| 4 ...
| 5 ...
| 6 ...
|_ 7 125.00 www.branzone.com (208.100.60.6) 41.874,-87.650 United States (Illinois)
|_whois-domain: You should provide a domain name.
| whois-ip: Record found at whois.arin.net
| netrange: 208.100.60.0 - 208.100.60.255
| netname: CHI-BRANZONE-INC-2
| custname: Branzone, Inc.
| country: US stateprov: IL
| orgtechname: Steadfast Networks Network Operations Center
|_orgtechemail: [email protected]
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 ... 6
7 125.00 ms www.branzone.com (208.100.60.6)
NSE: Script Post-scanning.
Initiating NSE at 19:29
Completed NSE at 19:29, 0.00s elapsed
Initiating NSE at 19:29
Completed NSE at 19:29, 0.00s elapsed
Initiating NSE at 19:29
Completed NSE at 19:29, 0.00s elapsed
Read data files from: C:\Program Files (x86)\Nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 3521.71 seconds
Raw packets sent: 6058 (238.170KB) | Rcvd: 129 (8.976KB)
|
|
|
|
VeteranXV
|
please tell me more of the great detective mystery adventures of Shift. I cannot wait.
|
|
|
|
VeteranXX
|
Quote:
Originally Posted by S_hift

|
download WinMTR and run it for at least 100 traces against nifleheims IP 208.100.45.13 and post the output
|
|
|
|
Sour++
Contributor
|
shift is giving me neg rep for this thread because of lol and me posting the youtube video he made while researching this subject
|
|
|
|
VeteranX
|
lemon is triggered by neg reps lol
|
|
|
|
Currently Active Users Viewing This Thread: 1 (0 members and 1 guests)
|
|
|
 Posting Rules
Posting Rules
|
You may not post new threads
You may not post replies
You may not post attachments
You may not edit your posts
HTML code is Off
|
|
|
AGENT: claudebot / Y
All times are GMT -4. The time now is 08:20.
|